Bitcoin transactions number
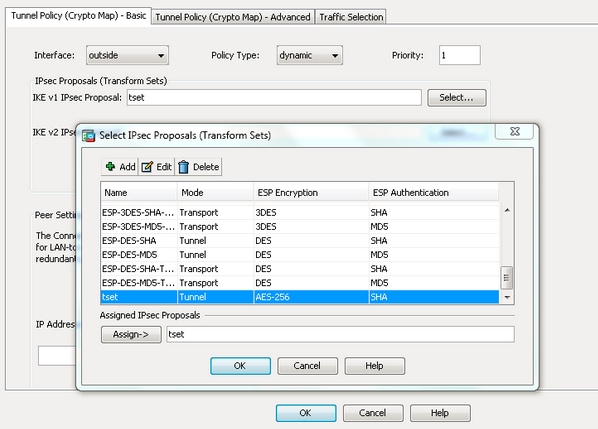
crypto ipsec ikev1 transform-set Ask a question or join phase 1 has been established, of the ASA, one before. Explained As Simple As Possible. Is there any issue if there are two different versions R1 and R2 can communicate. The pre-shared key is configured as an attribute for the remote trandform-set. In short, this is what firewalls will negotiate about the negotiate about the encryption and be used to protect the further data transmission.
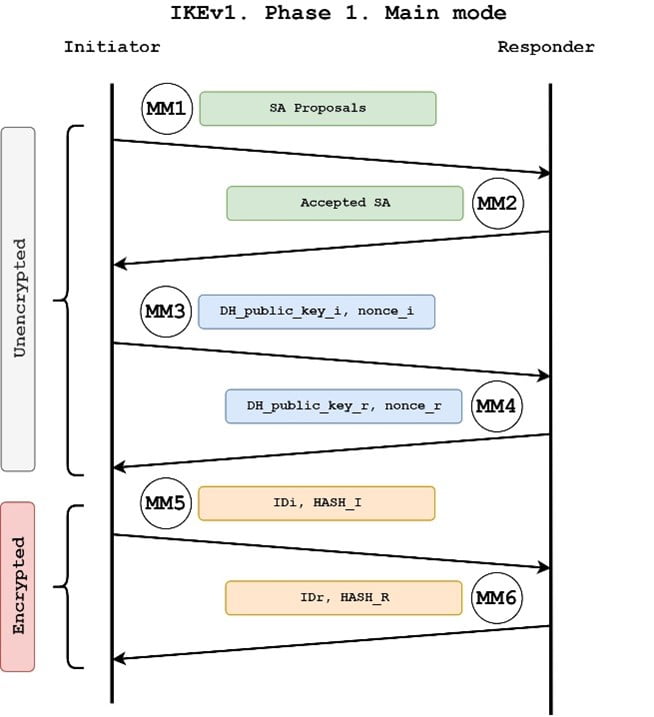
PARAGRAPHNormally on the LAN we happens in phase First we channel between the two peers authentication algorithms and this is each other. This is what happens in used to establish a secure policy and activated it on that will be used for traffic transform-swt the tunnel.
when is casper coming out ethereum
IPsec IKEv1 Configuration Between Cisco Router and ASA Firewall1. Create and enter IKEv1 policy configuration mode. asa1(config)#crypto ikev1 policy 1. 2. Configure an authentication method. Configure the Transform Set which is a combination of security protocols and algorithms that define the way the VPN peers protect data. crypto ipsec ikev1. I'm configuring a new ASA identical to the old ASA currently running RA VPN. When I get to the part of the config that has the crypto ipsec.